How To Access Local Users And Groups In Windows 10 Home
This browser is no longer supported.
Upgrade to Microsoft Edge to accept advantage of the latest features, security updates, and technical support.
Local Accounts
Applies to
- Windows 11
- Windows 10
- Windows Server 2019
- Windows Server 2016
This reference topic for It professionals describes the default local user accounts for servers, including how to manage these built-in accounts on a member or standalone server.
About local user accounts
Local user accounts are stored locally on the server. These accounts tin be assigned rights and permissions on a detail server, but on that server only. Local user accounts are security principals that are used to secure and manage admission to the resource on a standalone or member server for services or users.
This topic describes the following:
-
Default local user accounts
-
Ambassador business relationship
-
Guest Business relationship
-
HelpAssistant account (installed by using a Remote Assistance session)
-
DefaultAccount
-
-
Default local organization accounts
-
How to manage local accounts
-
Restrict and protect local accounts with administrative rights
-
Enforce local business relationship restrictions for remote access
-
Deny network logon to all local Administrator accounts
-
Create unique passwords for local accounts with administrative rights
-
For information about security principals, encounter Security Principals.
Default local user accounts
The default local user accounts are built-in accounts that are created automatically when y'all install Windows.
Later Windows is installed, the default local user accounts cannot be removed or deleted. In add-on, default local user accounts do not provide access to network resources.
Default local user accounts are used to manage access to the local server'due south resources based on the rights and permissions that are assigned to the account. The default local user accounts, and the local user accounts that you create, are located in the Users binder. The Users folder is located in the Local Users and Groups binder in the local Computer Direction Microsoft Management Panel (MMC). Computer Management is a collection of administrative tools that you can employ to manage a single local or remote figurer. For more data, run into How to manage local accounts later in this topic.
Default local user accounts are described in the post-obit sections.
Administrator business relationship
The default local Administrator business relationship is a user business relationship for the system ambassador. Every figurer has an Administrator account (SID S-1-5-domain-500, brandish name Ambassador). The Ambassador account is the first account that is created during the Windows installation.
The Administrator account has total control of the files, directories, services, and other resources on the local computer. The Ambassador account can create other local users, assign user rights, and assign permissions. The Administrator account can take command of local resources at any time simply by changing the user rights and permissions.
The default Ambassador account cannot be deleted or locked out, but information technology can be renamed or disabled.
From Windows 10, Windows eleven and Windows Server 2016, Windows setup disables the born Ambassador account and creates some other local account that is a member of the Administrators group. Members of the Administrators groups tin run apps with elevated permissions without using the Run as Administrator option. Fast User Switching is more secure than using Runas or different-user elevation.
Business relationship group membership
By default, the Ambassador account is installed as a fellow member of the Administrators group on the server. It is a best practice to limit the number of users in the Administrators group considering members of the Administrators grouping on a local server have Full Control permissions on that computer.
The Administrator business relationship cannot be deleted or removed from the Administrators group, simply it tin be renamed.
Security considerations
Because the Administrator business relationship is known to exist on many versions of the Windows operating system, it is a best practice to disable the Ambassador account when possible to make it more difficult for malicious users to gain access to the server or client computer.
You can rename the Ambassador account. However, a renamed Administrator account continues to use the same automatically assigned security identifier (SID), which tin be discovered by malicious users. For more data well-nigh how to rename or disable a user account, see Disable or activate a local user account and Rename a local user account.
As a security all-time practice, use your local (non-Administrator) account to sign in and then use Run equally administrator to attain tasks that require a college level of rights than a standard user account. Do non use the Ambassador account to sign in to your computer unless it is entirely necessary. For more information, see Run a program with administrative credentials.
In comparison, on the Windows customer operating system, a user with a local user business relationship that has Ambassador rights is considered the system administrator of the customer computer. The first local user account that is created during installation is placed in the local Administrators grouping. However, when multiple users run as local administrators, the IT staff has no control over these users or their customer computers.
In this case, Group Policy can be used to enable secure settings that tin command the use of the local Administrators group automatically on every server or customer figurer. For more data about Grouping Policy, see Group Policy Overview.
Of import
-
Bare passwords are non allowed in the versions designated in the Applies To list at the start of this topic.
-
Even when the Ambassador account has been disabled, it tin can however exist used to gain admission to a computer by using safe fashion. In the Recovery Console or in safe mode, the Administrator account is automatically enabled. When normal operations are resumed, it is disabled.
Guest account
The Guest account is disabled by default on installation. The Guest business relationship lets occasional or former users, who do not accept an account on the calculator, temporarily sign in to the local server or customer figurer with limited user rights. By default, the Guest business relationship has a blank password. Because the Guest business relationship can provide anonymous access, information technology is a security run a risk. For this reason, information technology is a best practise to leave the Guest account disabled, unless its utilize is entirely necessary.
Business relationship group membership
Past default, the Guest account is the but fellow member of the default Guests group (SID S-i-5-32-546), which lets a user sign in to a server. On occasion, an administrator who is a member of the Administrators group can gear up a user with a Invitee account on one or more computers.
Security considerations
When enabling the Guest account, only grant express rights and permissions. For security reasons, the Guest account should non be used over the network and made accessible to other computers.
In improver, the invitee user in the Guest business relationship should not exist able to view the effect logs. Later on the Guest account is enabled, it is a best do to monitor the Guest business relationship frequently to ensure that other users cannot apply services and other resources, such equally resource that were unintentionally left available by a previous user.
HelpAssistant business relationship (installed with a Remote Assistance session)
The HelpAssistant account is a default local account that is enabled when a Remote Help session is run. This account is automatically disabled when no Remote Aid requests are pending.
HelpAssistant is the primary business relationship that is used to constitute a Remote Aid session. The Remote Assistance session is used to connect to another computer running the Windows operating organisation, and it is initiated by invitation. For solicited remote assistance, a user sends an invitation from their estimator, through electronic mail or as a file, to a person who can provide aid. After the user's invitation for a Remote Assistance session is accepted, the default HelpAssistant account is automatically created to give the person who provides assistance limited access to the computer. The HelpAssistant account is managed by the Remote Desktop Aid Session Manager service.
Security considerations
The SIDs that pertain to the default HelpAssistant account include:
-
SID: S-1-5-<domain>-13, display name Terminal Server User. This group includes all users who sign in to a server with Remote Desktop Services enabled. Note that, in Windows Server 2008, Remote Desktop Services are chosen Concluding Services.
-
SID: S-i-v-<domain>-xiv, display name Remote Interactive Logon. This grouping includes all users who connect to the computer by using a remote desktop connection. This group is a subset of the Interactive grouping. Access tokens that contain the Remote Interactive Logon SID as well comprise the Interactive SID.
For the Windows Server operating system, Remote Assistance is an optional component that is non installed past default. You must install Remote Assistance before information technology can be used.
For details about the HelpAssistant account attributes, see the post-obit tabular array.
HelpAssistant account attributes
| Attribute | Value |
|---|---|
| Well-Known SID/RID | S-1-5-<domain>-13 (Terminal Server User), S-1-5-<domain>-fourteen (Remote Interactive Logon) |
| Blazon | User |
| Default container | CN=Users, DC=<domain>, DC= |
| Default members | None |
| Default member of | Domain Guests Guests |
| Protected by ADMINSDHOLDER? | No |
| Condom to move out of default container? | Can be moved out, but we exercise not recommend information technology. |
| Rubber to consul direction of this grouping to non-Service admins? | No |
DefaultAccount
The DefaultAccount, as well known as the Default System Managed Account (DSMA), is a built-in business relationship introduced in Windows 10 version 1607 and Windows Server 2016. The DSMA is a well-known user account blazon. It is a user neutral account that can exist used to run processes that are either multi-user aware or user-agnostic. The DSMA is disabled by default on the desktop SKUs (total windows SKUs) and WS 2016 with the Desktop.
The DSMA has a well-known RID of 503. The security identifier (SID) of the DSMA will thus have a well-known SID in the following format: South-1-5-21-<ComputerIdentifier>-503
The DSMA is a fellow member of the well-known group Organisation Managed Accounts Group, which has a well-known SID of Due south-one-5-32-581.
The DSMA alias tin can be granted admission to resources during offline staging even before the account itself has been created. The business relationship and the group are created during get-go kicking of the auto within the Security Accounts Manager (SAM).
How Windows uses the DefaultAccount
From a permission perspective, the DefaultAccount is a standard user account. The DefaultAccount is needed to run multi-user-manifested-apps (MUMA apps). MUMA apps run all the time and react to users signing in and signing out of the devices. Unlike Windows Desktop where apps run in context of the user and go terminated when the user signs off, MUMA apps run by using the DSMA.
MUMA apps are functional in shared session SKUs such as Xbox. For example, Xbox vanquish is a MUMA app. Today, Xbox automatically signs in as Guest business relationship and all apps run in this context. All the apps are multi-user-aware and respond to events fired by user manager. The apps run as the Guest account.
Similarly, Phone auto logs in every bit a "DefApps" business relationship which is akin to the standard user account in Windows but with a few extra privileges. Brokers, some services and apps run equally this business relationship.
In the converged user model, the multi-user-enlightened apps and multi-user-aware brokers will demand to run in a context different from that of the users. For this purpose, the organisation creates DSMA.
How the DefaultAccount gets created on domain controllers
If the domain was created with domain controllers that run Windows Server 2016, the DefaultAccount will exist on all domain controllers in the domain. If the domain was created with domain controllers that run an earlier version of Windows Server, the DefaultAccount will exist created afterward the PDC Emulator role is transferred to a domain controller that runs Windows Server 2016. The DefaultAccount will so be replicated to all other domain controllers in the domain.
Recommendations for managing the Default Account (DSMA)
Microsoft does not recommend changing the default configuration, where the business relationship is disabled. At that place is no security risk with having the account in the disabled state. Changing the default configuration could hinder hereafter scenarios that rely on this account.
Default local system accounts
Organisation
The SYSTEM account is used past the operating system and by services that run under Windows. In that location are many services and processes in the Windows operating system that need the capability to sign in internally, such every bit during a Windows installation. The SYSTEM account was designed for that purpose, and Windows manages the Organization account's user rights. It is an internal account that does not evidence up in User Managing director, and information technology cannot be added to any groups.
On the other hand, the SYSTEM account does announced on an NTFS file system volume in File Director in the Permissions portion of the Security menu. By default, the SYSTEM account is granted Full Control permissions to all files on an NTFS volume. Here the Arrangement account has the aforementioned functional rights and permissions equally the Ambassador account.
Note
To grant the account Administrators group file permissions does not implicitly give permission to the Organisation account. The SYSTEM account'due south permissions tin exist removed from a file, but we do not recommend removing them.
NETWORK SERVICE
The NETWORK SERVICE account is a predefined local account used past the service control director (SCM). A service that runs in the context of the NETWORK SERVICE account presents the estimator's credentials to remote servers. For more information, see NetworkService Account.
LOCAL SERVICE
The LOCAL SERVICE account is a predefined local account used past the service command manager. It has minimum privileges on the local computer and presents bearding credentials on the network. For more data, see LocalService Business relationship.
How to manage local user accounts
The default local user accounts, and the local user accounts that y'all create, are located in the Users folder. The Users folder is located in Local Users and Groups. For more data well-nigh creating and managing local user accounts, see Manage Local Users.
You can utilise Local Users and Groups to assign rights and permissions on the local server, and that server only, to limit the ability of local users and groups to perform certain actions. A right authorizes a user to perform sure actions on a server, such as backing up files and folders or shutting down a server. An access permission is a rule that is associated with an object, usually a file, folder, or printer. Information technology regulates which users can have access to an object on the server and in what manner.
You cannot use Local Users and Groups on a domain controller. Notwithstanding, you can use Local Users and Groups on a domain controller to target remote computers that are not domain controllers on the network.
Annotation
You apply Active Directory Users and Computers to manage users and groups in Active Directory.
You can also manage local users past using NET.EXE USER and manage local groups past using NET.EXE LOCALGROUP, or by using a variety of PowerShell cmdlets and other scripting technologies.
Restrict and protect local accounts with administrative rights
An administrator can use a number of approaches to prevent malicious users from using stolen credentials, such as a stolen password or password hash, for a local account on i computer from being used to authenticate on another computer with administrative rights; this is besides called "lateral motility".
The simplest approach is to sign in to your estimator with a standard user account, instead of using the Ambassador business relationship for tasks, for case, to browse the Net, ship email, or use a word processor. When y'all want to perform an authoritative task, for example, to install a new program or to change a setting that affects other users, you lot don't take to switch to an Administrator account. Y'all tin can employ User Business relationship Command (UAC) to prompt you for permission or an ambassador countersign before performing the task, every bit described in the side by side section.
The other approaches that can be used to restrict and protect user accounts with authoritative rights include:
-
Enforce local business relationship restrictions for remote access.
-
Deny network logon to all local Administrator accounts.
-
Create unique passwords for local accounts with administrative rights.
Each of these approaches is described in the post-obit sections.
Notation
These approaches practice not employ if all authoritative local accounts are disabled.
Enforce local account restrictions for remote access
The User Account Command (UAC) is a security characteristic in Windows that has been in use in Windows Server 2008 and in Windows Vista, and the operating systems to which the Applies To listing refers. UAC enables you to stay in command of your computer by informing you when a program makes a change that requires administrator-level permission. UAC works by adjusting the permission level of your user account. Past default, UAC is set to notify yous when applications try to make changes to your reckoner, simply y'all can change how often UAC notifies you.
UAC makes it possible for an account with administrative rights to be treated as a standard user non-ambassador account until full rights, besides called elevation, is requested and approved. For instance, UAC lets an administrator enter credentials during a non-ambassador's user session to perform occasional administrative tasks without having to switch users, sign out, or apply the Run as command.
In improver, UAC can require administrators to specifically corroborate applications that brand system-wide changes before those applications are granted permission to run, even in the administrator's user session.
For example, a default feature of UAC is shown when a local business relationship signs in from a remote calculator past using Network logon (for example, by using Cyberspace.EXE Utilize). In this example, it is issued a standard user token with no administrative rights, but without the ability to request or receive elevation. Consequently, local accounts that sign in by using Network logon cannot access administrative shares such as C$, or ADMIN$, or perform any remote administration.
For more data about UAC, see User Account Control.
The post-obit tabular array shows the Group Policy and registry settings that are used to enforce local account restrictions for remote admission.
| No. | Setting | Detailed Description |
|---|---|---|
| Policy location | Figurer Configuration\Windows Settings\Security Settings\Local Policies\Security Options | |
| ane | Policy proper noun | User Account Control: Run all administrators in Admin Approval Mode |
| Policy setting | Enabled | |
| ii | Policy location | Computer Configuration\Windows Settings\Security Settings\Local Policies\Security Options |
| Policy name | User Account Command: Run all administrators in Admin Approving Mode | |
| Policy setting | Enabled | |
| 3 | Registry key | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Registry value proper noun | LocalAccountTokenFilterPolicy | |
| Registry value type | DWORD | |
| Registry value information | 0 |
Note
You tin as well enforce the default for LocalAccountTokenFilterPolicy past using the custom ADMX in Security Templates.
To enforce local account restrictions for remote admission
-
Start the Group Policy Direction Panel (GPMC).
-
In the console tree, expand <Forest>\Domains\<Domain>, and so Group Policy Objects where woods is the name of the forest, and domain is the name of the domain where you want to set up the Grouping Policy Object (GPO).
-
In the console tree, correct-click Group Policy Objects, and > New.
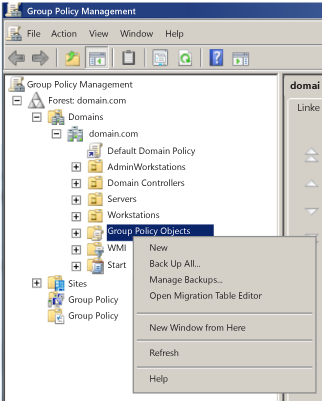
-
In the New GPO dialog box, blazon <gpo_name>, and > OK where gpo_name is the proper noun of the new GPO. The GPO name indicates that the GPO is used to restrict local administrator rights from existence carried over to another computer.

-
In the details pane, right-click <gpo_name>, and > Edit.

-
Ensure that UAC is enabled and that UAC restrictions apply to the default Administrator account past doing the following:
-
Navigate to the Reckoner Configuration\Windows Settings\Security Settings\Local Policies\, and > Security Options.
-
Double-click User Account Control: Run all administrators in Admin Approval Way > Enabled > OK.
-
Double-click User Account Control: Admin Blessing Mode for the Built-in Administrator account > Enabled > OK.
-
-
Ensure that the local account restrictions are applied to network interfaces by doing the post-obit:
-
Navigate to Computer Configuration\Preferences and Windows Settings, and > Registry.
-
Right-click Registry, and > New > Registry Item.

-
In the New Registry Properties dialog box, on the General tab, alter the setting in the Action box to Supervene upon.
-
Ensure that the Hive box is prepare to HKEY_LOCAL_MACHINE.
-
Click (…), browse to the following location for Key Path > Select for: SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System.
-
In the Value name area, type LocalAccountTokenFilterPolicy.
-
In the Value blazon box, from the drop-down list, select REG_DWORD to change the value.
-
In the Value information box, ensure that the value is set to 0.
-
Verify this configuration, and > OK.

-
-
Link the GPO to the outset Workstations organizational unit (OU) by doing the post-obit:
-
Navigate to the <Forest>\Domains\<Domain>\OU path.
-
Correct-click the Workstations OU, and > Link an existing GPO.

-
Select the GPO that you lot just created, and > OK.
-
-
Exam the functionality of enterprise applications on the workstations in that first OU and resolve whatever problems acquired by the new policy.
-
Create links to all other OUs that contain workstations.
-
Create links to all other OUs that comprise servers.
Deny network logon to all local Administrator accounts
Denying local accounts the ability to perform network logons can help prevent a local account password hash from being reused in a malicious assault. This procedure helps to prevent lateral movement past ensuring that the credentials for local accounts that are stolen from a compromised operating system cannot exist used to compromise additional computers that use the same credentials.
Notation
To perform this process, you must offset place the name of the local, default Administrator business relationship, which might non be the default user proper noun "Ambassador", and any other accounts that are members of the local Administrators grouping.
The following table shows the Group Policy settings that are used to deny network logon for all local Ambassador accounts.
| No. | Setting | Detailed Description |
|---|---|---|
| Policy location | Computer Configuration\Windows Settings\Security Settings\Local Policies\User Rights Consignment | |
| 1 | Policy proper noun | Deny access to this computer from the network |
| Policy setting | Local account and fellow member of Administrators grouping | |
| ii | Policy location | Computer Configuration\Windows Settings\Security Settings\Local Policies\User Rights Assignment |
| Policy name | Deny log on through Remote Desktop Services | |
| Policy setting | Local account and member of Administrators group |
To deny network logon to all local administrator accounts
-
Start the Group Policy Direction Panel (GPMC).
-
In the console tree, expand <Forest>\Domains\<Domain>, and and then Group Policy Objects, where forest is the name of the forest, and domain is the name of the domain where you desire to fix the Grouping Policy Object (GPO).
-
In the console tree, right-click Group Policy Objects, and > New.
-
In the New GPO dialog box, type <gpo_name>, then > OK where gpo_name is the proper name of the new GPO indicates that it is beingness used to restrict the local administrative accounts from interactively signing in to the computer.

-
In the details pane, right-click <gpo_name>, and > Edit.

-
Configure the user rights to deny network logons for authoritative local accounts equally follows:
-
Navigate to the Computer Configuration\Windows Settings\Security Settings\, and > User Rights Assignment.
-
Double-click Deny access to this computer from the network.
-
Click Add User or Group, type Local account and member of Administrators group, and > OK.
-
-
Configure the user rights to deny Remote Desktop (Remote Interactive) logons for authoritative local accounts every bit follows:
-
Navigate to Computer Configuration\Policies\Windows Settings and Local Policies, and then click User Rights Assignment.
-
Double-click Deny log on through Remote Desktop Services.
-
Click Add User or Group, type Local account and member of Administrators group, and > OK.
-
-
Link the GPO to the first Workstations OU as follows:
-
Navigate to the <Woods>\Domains\<Domain>\OU path.
-
Right-click the Workstations OU, and > Link an existing GPO.
-
Select the GPO that you lot merely created, and > OK.
-
-
Test the functionality of enterprise applications on the workstations in that first OU and resolve any problems acquired by the new policy.
-
Create links to all other OUs that contain workstations.
-
Create links to all other OUs that contain servers.
Note
Yous might have to create a divide GPO if the user proper noun of the default Ambassador account is dissimilar on workstations and servers.
Create unique passwords for local accounts with authoritative rights
Passwords should be unique per individual account. While this is by and large true for private user accounts, many enterprises accept identical passwords for mutual local accounts, such as the default Administrator account. This also occurs when the same passwords are used for local accounts during operating system deployments.
Passwords that are left unchanged or changed synchronously to keep them identical add a meaning chance for organizations. Randomizing the passwords mitigates "pass-the-hash" attacks by using different passwords for local accounts, which hampers the ability of malicious users to use password hashes of those accounts to compromise other computers.
Passwords tin can be randomized by:
-
Purchasing and implementing an enterprise tool to achieve this job. These tools are commonly referred to as "privileged countersign management" tools.
-
Configuring Local Administrator Password Solution (LAPS) to accomplish this task.
-
Creating and implementing a custom script or solution to randomize local account passwords.
See besides
The post-obit resources provide additional information about technologies that are related to local accounts.
-
Security Principals
-
Security Identifiers
-
Access Control Overview
Feedback
Submit and view feedback for
How To Access Local Users And Groups In Windows 10 Home,
Source: https://docs.microsoft.com/en-us/windows/security/identity-protection/access-control/local-accounts
Posted by: eastlandrodut1948.blogspot.com


0 Response to "How To Access Local Users And Groups In Windows 10 Home"
Post a Comment